- By Rosan Baral
- Updated On -
- 34 Comments
- Reading Time: 28 Minutes
The topic for today is Website Security, and it’s interesting as well as challenging to discuss as it changes every minute or even seconds.
The popular queries around the internet;
- How to secure a website?
- How to implement web application security?
- Is this website safe?
This comprehensive guide provides a clear framework for site owners to secure their websites from hackers and security vulnerabilities.
Table of Content
Before diving into in-depth strategies, let’s know about website security’s general aspects.
What is Website Security?
Website security is a managed process or action taken to protect a website from different attacks or exploitation. It is an ongoing strategy and a crucial part of website management.
Why is Website Security Important?
Let’s put this discussion with an example first.
The Question: What would happen if you leave your home unattended or unlocked when you are away?
The Answer: There is a 50/50 chance that either your home gets robbed and smashed, or nothing happens because it’s your lucky day.

We hope you and your family and friends don’t have to deal with this situation in the real world and wish you are lucky every day.
But the same thing can’t be assumed for the security of your website.
There are numerous ways people or bots can attack your site or web application.
So, you must take web security as a serious threat. Why?
- To protect it from hack attempts and malware.
- To prevent a data breach for your clients or business.
- To improve your search engine rankings.
- To stop attackers from abusing web server resources.
- To block phishing campaign emails from your website and lots of other reasons.
You have put a considerable amount of time and effort into your website. What would happen to your online presence if an attacker gains access to your website?
So, you need to implement active security measures to defend against these attacks and improve website security.
Companies spend millions on security, and it’s money wasted. None of these measures addresses the weakest link in the security chain - Kevin Mitnick ( The World’s Most Famous Hacker)
Why and How do Websites Get Hacked?
According to Internet Live Stats and Google, “There are over 1.73 Billion websites on the internet, and over 113,000 websites get hacked daily.
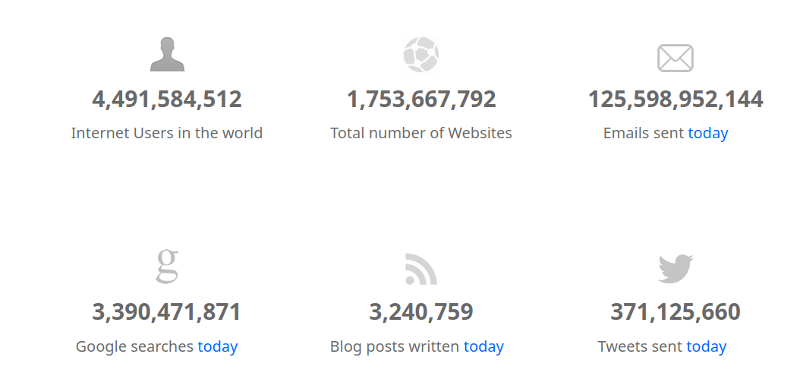
Depending on who you are, the results can vary. Some of the main reasons;
- Commercial Gain – Your competitors or enemies can benefit from your downfall. What would happen if Google Chrome gets hacked today? Bing gets the audience. Just saying!
- System Resources – The business of renting system resources is a big trade and a huge motivator for many cyber groups.
- For Fun – There is a good chance that sometimes these attackers are computer-savvy people with nothing else to do except hack websites.
- Online Protest – Hacktivists will damage websites to gain attention and spread their word instead of yelling and burning wheels on the streets.
- Money – Does this need an explanation? I don’t think so.
You can be sure that website security threats are here to stay, and hacking will get advanced every minute or second, day by day.
But to operate and be successful with the hacking attempts, one needs to break the barrier between the web servers and applications.
But how exactly do websites get hacked?
There are millions of ways that a website can get hacked. It’s a vast issue in reality.
Cyber-threat is mainly a reflection of our weaknesses. An accurate vision of digital and behavioral gaps is crucial for a consistent cyber-resilience - Stephane Nappo
The most common and popular ways a website can get hacked are listed below;
- Data Leakage – The biggest issue is Data Leakage in today’s online world. A famous example would be the Data Breach of Linkedin, where 117 Million accounts were compromised and sold on the black market.
- Weak Passwords – This is the easiest way to lose access to your login credentials. A weak password can easily be decrypted with today’s technological advancement.
- No Regular Updates – In addition to fixing bugs or glitches, the regular updates typically come with security enhancements. People make the mistake of implementing inconsistent updates.
- Not Limiting User Permissions – Neglecting to limit the user permissions can be a recipe for disaster. Not every employee or client of your business should have access to your server configuration.
- Using Insecure Protocols – Protocols might include not using encryption technology, visiting untrusted websites, weak web server security, and cracked software.
Even though there are several methods by which websites can get infected, the number one reason would be negligence from people.
And second would be poor code implementation in general.
There are two typical ways people use precautions for website security;
- Precautions used after the incident.
- Precautions used before the incident.
Let’s compare these topics to human health for easy understanding.
Would you prefer to take care of your teeth and avoid a dentist visit, or would you choose not to give a damn about your teeth and wait for a dentist’s visit?
As you can notice, it ultimately comes to your personal preferences. Still, even though it’s about your preferences, it’s a wise decision to take care of your teeth and avoid visiting a dentist.
On the contrary, it would be profitable for your health.
Ultimately, you can save an ample amount of time and money.
So, you can see for yourself why you need to be one step ahead of your attackers.
The same philosophy integrates with website security. It’s nearly impossible for any website to be 100% secure in today’s context, but you can make this challenging for attackers.
You should know that recovering a hacked website is more expensive than managing a web security plan beforehand.
Consider your website as a "Glass" in an online world. You need to polish it every day and try to make it shiny compared to your competition so that your audiences can see through your website.
You need to be aware that there are many ways to join a broken glass, but it will leave a mark on its structure once broken.
So, it’s wise to protect your website beforehand, then wait for the disaster to arrive your way.
Now that you have a rough idea of how web security works, let’s dive into strategies to mitigate risk and implement security protocols for your site security.
Website Vulnerabilities and Mitigation Plans
A website can get hacked or attacked due to many factors. Still, some of the leading and widely used cyberattacks are discussed below.
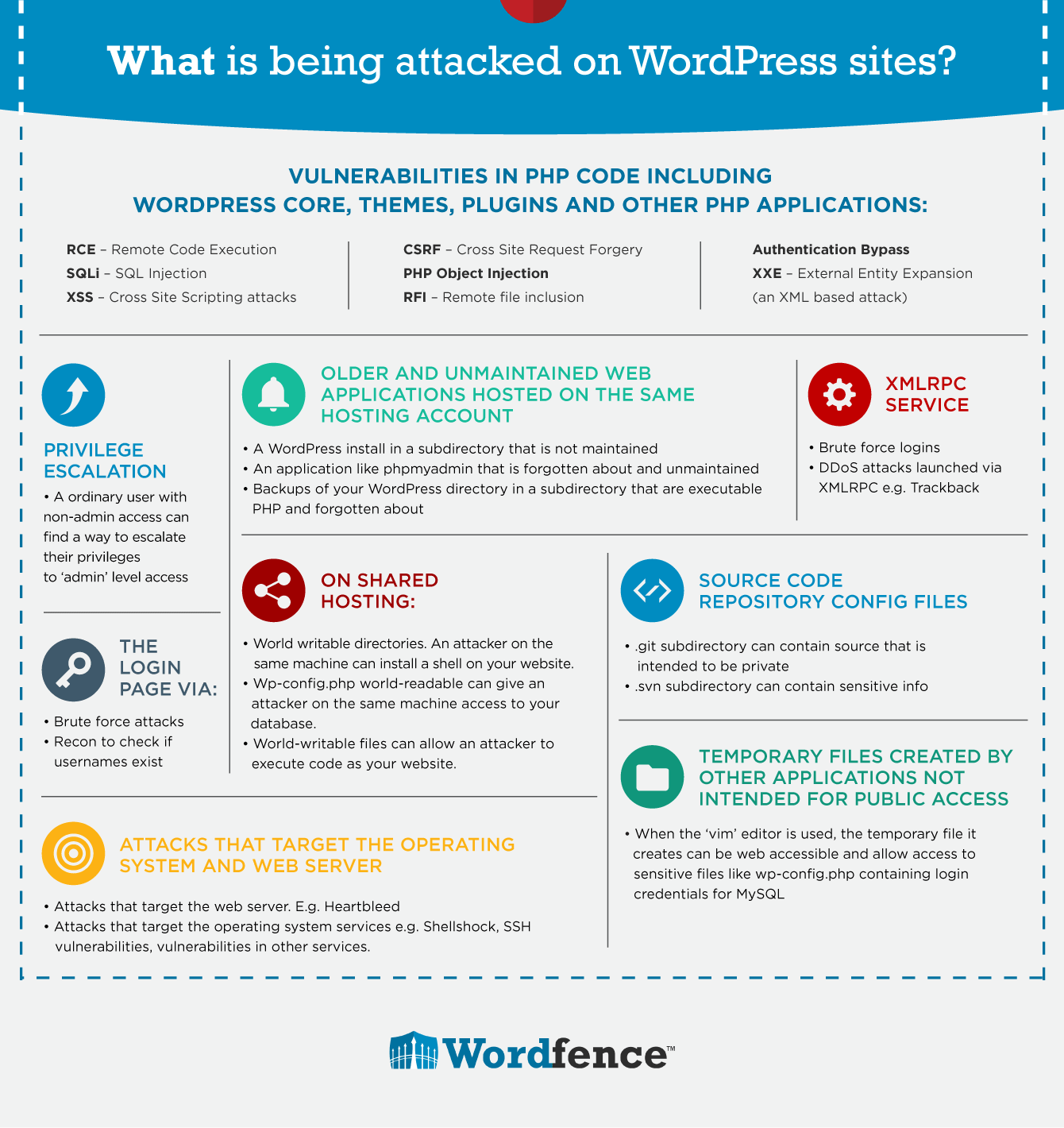
1) SQL Injections
These types of injection attacks are very effective. The attacker attempts to access or alter the user input or SQL query of a web system by manipulating the user-supplied data to a website database.
This attack is a high-risk threat because, if successful, the attacker can alter the user-submitted data to his desired outcome instead of the information expected from the website database.
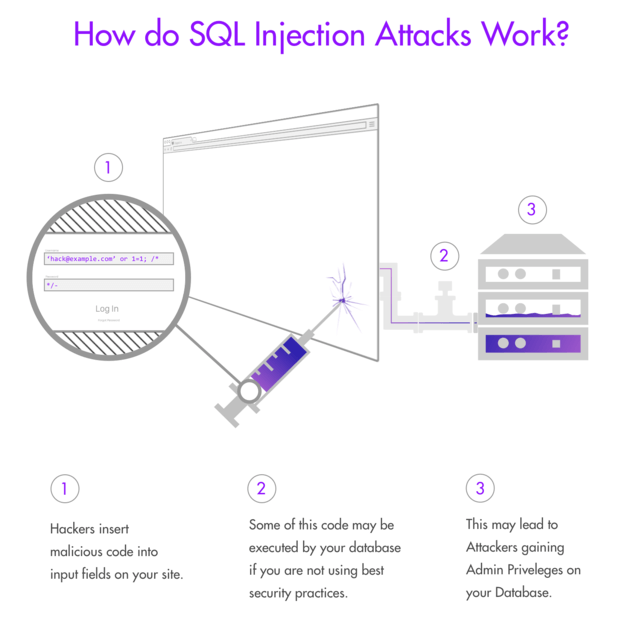
What are the impacts?
- Sensitive data from the website database, including personal information and hash files, can be read.
- Database queries can be altered. They can be edited, deleted, or even updated.
- An attacker can obtain persistent backdoor access into an organization’s systems in some circumstances.
What are the mitigation plan to prevent SQL Injection?
- Use prepared or parameterized queries.
- Validate user input data.
- Limit user privileges.
- Use stored procedures.
- Hide info about the error message.
- Encrypt database credentials and store them in a separate path.
- Disable shell access and other related functionalities if not in use.
To avoid a SQL Injection Attack, you always need to be cautious and be prepared for the worst. Don’t forget to validate and sanitize all the user interactions.
2) Cross-Site Scripting
Cross-Site Scripting is also known as XSS Attack in a technical term.
These security vulnerabilities usually inject a malicious script that is executed on the client-side, such as a browser or application’s output.
These flaws can occur when the application or script takes untrusted data and sends it through a web browser or application without any proper validation.
These flaws could potentially lead to a site takeover.
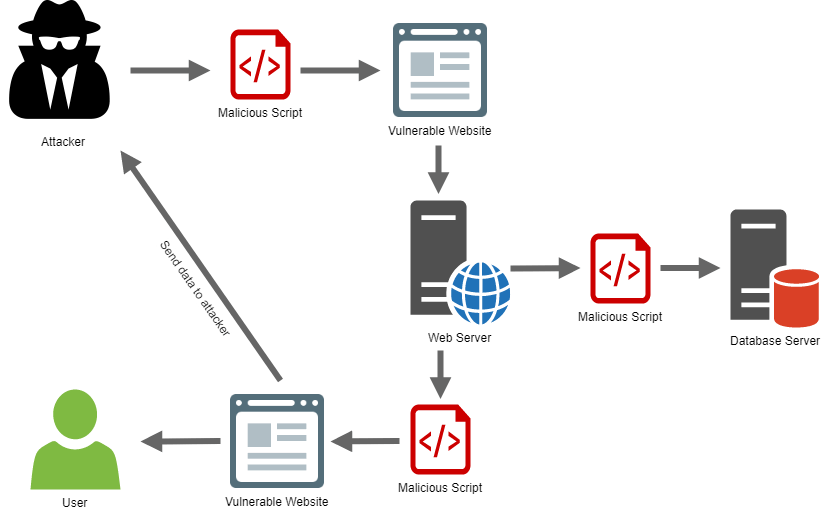
What are the impacts?
- XSS Attack can result in the user’s session cookie being disclosed. It allows attackers to take over the user’s account and manipulate their sessions.
- Disclosure of end user’s files.
- Install malware and spyware.
- Leakage of sensitive data.
- Creating falsified information and targeting client-side users.
What are the mitigation plan to prevent Cross-Site Scripting?
While cross-site scripting attacks can be hard to predict and detect, the best practice would be to validate and sanitize the vulnerabilities.
It will help to utilize web application firewalls to reduce and prevent XSS attacks.
3) Brute Force Attacks
These attacks attempt to crack down on login credentials from a published or hidden web page, again and again, until the attackers get access to their source.
Guessing login credentials for a particular site or source can take a long time.
Hence, hackers and organizations have developed tools to do their job faster and easier.
You should know that the outcome would be catastrophic if the attackers accessed your credentials.

What are the mitigation plan to prevent Brute Force Attacks?
- Use a complex password.
- Protect your personal information.
- Limit the login attempts.
- Modify and secure .htaccess file with appropriate file permissions.
- Use honeypot or captcha.
- Utilize two-factor authentication.
- Use content delivery networks (CDNs).
- Deploy web application firewalls (WAF).
Preventing and neutralizing a brute force attack in progress is the best counter-attack strategy than waiting for attackers to have access to your network or source.
4) Malware Infections
Malware is a type of software or source code that attempts to steal user credentials or manipulate the user’s computer to do things that users don’t intend to do.
Malware infections are used by many to attack and infect websites and are a severe security threat.
Malware infections often lead to severe consequences, causing the victim’s computer to become slow or unresponsive. This leads to a website takeover.
What are the impacts?
- You can see unwanted ads while unusual changes to your website appearance.
- Your audiences can be redirected to other sites that could be malicious.
- They can drop backdoor access to attack your website.
- Attackers can place spam content and use SEO spam techniques to divert your site traffic to other sites.
- Your reputation, business sales, web traffic, and brand identity will likely take a hit if your website is infected with malware.
What are the mitigation plan to prevent Malware Infections?
- Install updates and patches promptly.
- Maintain regular backup of your website.
- Use Anti-Malware software or related software.
- A website’s risk of infections increases with the features and functionality. So, only use the features or functionality you need.
- If there is no need, disable file uploads for better online security.
- Try to use an automated patching system and threat intelligence service.
Cybercriminals don’t rest, and they will do their best to defame your website and your reputation all over.
You can protect your website against those cyberattacks with a web security service provider that is one step ahead of them.
5) Security Settings Misconfiguration
Security Settings are critical and must be defined and deployed for the web servers, applications, databases, cookies, and framework platforms.
In simple words, security misconfiguration merely is incorrectly constructing the file permissions or rules for your files and folders.
If these settings are not correctly configured, then it’s a free meal ticket for an attacker to get unauthorized access to sensitive data or functionality of your website.
What are the impacts?
I know automatic cars are already a reality in today’s world, but let’s talk about a manually handled car for our discussion.
What would happen if you put your car in neutral mode and let it roll down a steep hill without a driver inside it?
The consequences will be disastrous!
Likewise, suppose a web application lacks proper security protocols. In that case, an attacker can access the default accounts, unused web pages, unprotected directories, or exploit unpatched flaws.
If that happens, they can gain unauthorized access to your systems.
What are the mitigation plan to prevent Security Settings Configuration?
- Disable default accounts and passwords.
- Keep your software updated with regular security patches.
- Hire a professional to do the security hardening process for your website to be on the safe side.
- Don’t present stack tracers to your website users or audiences.
- Run automated tools and perform regular internal audits to identify security loopholes in the server configuration.
Website security tools are much more complex and advanced today. So, you need to be updated with the latest security trend in the markets.
6) Lack of Encryption Technology
Information exchanged between the user and the server must be served through a secure socket layer using encryption technology.
Web applications frequently transmit sensitive information or credentials like user authentication details, cookies, credit card information, and session tokens over a network layer.
Don’t make the mistake of using weak algorithms, expired or invalid certificates, and non-functional hard drive encryption technology for data transmission between your web server and your audience.
What would be the impact if your audience gets exposed to cyberattacks?
Your reputation would be destroyed, and you could be in trouble with legal departments to make it worse.

What are the mitigation plan to prevent the lack of Encryption Technology?
You should use SSL Certificate and Encryption Technology services for your website. Even if you do not handle sensitive information like credit cards, it is essential.
It provides privacy, data integrity, and critical security for your website and users’ personal information.
7) DDoS Attacks
DDoS, also known as Distributed Denial of Service, is an attack that makes a site unavailable with automated or manual fake requests and web traffic.
DDoS attacks are non-intrusive internet attacks on web servers that can cost websites thousands of dollars.
Typically, nothing is hacked while a website is under DDoS Attacks.
The primary purpose and impact of these types of attacks are to flood your server with web traffic to overcrowd your web server and make it inaccessible to your audience.
What would be the outcome if Facebook, Youtube, or Google went offline for about 10 minutes?
Just imagine the burst!
Unfortunately, if you fall victim to DDoS Attacks, you are likely to be attacked again.
According to Imperva Studies, they found out that two-thirds of DDoS attacks were hit repeatedly.
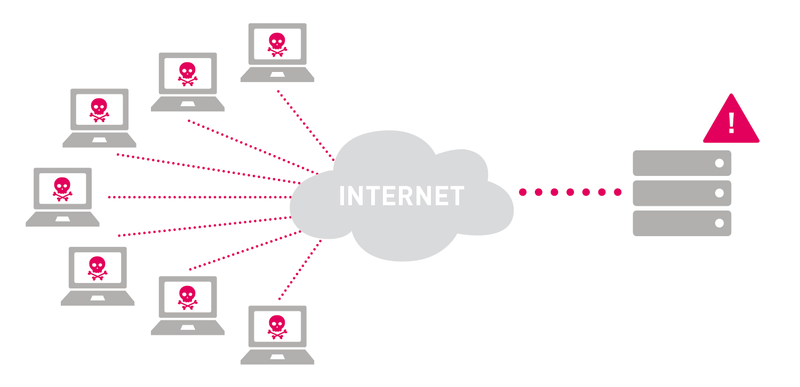
What are the mitigation plan to prevent DDoS Attacks?
In reality, the only way to get rid of the DDoS attack is to engage in a counter-attack strategy.
If a web server can throw more resources behind a website than the attacks, there is a good chance that the site stays up.
Otherwise, it will go down and be unavailable.
Let’s say you have a web server that can host around 25,000 simultaneous requests on any given day.
Then suddenly, some programmed bots attack your website with over 30,000 fake requests per hour. If that’s the case, would you be able to stop the attacks?
No, it’s impossible to stop such kinds of DDoS attacks with your available web resources.
In those cases, it’s wise to consult a web security expert for help or use a Web Application Firewall to secure your website from DDoS Attacks.
Website Protection Best Practices
When building an online presence for your business, you must be well-prepared in advance and have a well-managed strategy beforehand.
Due to high competition in today’s business markets, you can’t afford to make the mistake of “I will see when the time comes” philosophy.
Everyone can predict and fantasize about the future, but until now, no one exactly knows about the future.
No one can give you a guarantee to secure your website without any obstacles.
However, there are methods that companies or individuals can implement to help reduce the chance of running into web security dilemmas.
1) Create a Blueprint
Site owners and web developers need to make pre-planned arrangements from the very beginning for better online security for their websites.
All too often, taking a disorganized approach to the situation will gain next to nothing.

Sit down with your IT security team or consult a web security expert about developing a detailed and actionable web application security plan.
2) Use Secure Hosting Provider
Out of the many factors, web server-level security plays an essential role in your website security?
Hacking websites will be an easy task for attackers if you have a weak web hosting provider.
Even though you make every detailed effort to secure your website, you can be in trouble if you are weak in server-level security.
So, you must choose a host that you can trust with your website.
It takes multiple website firewalls, server configuration, and security measures to ensure that your website’s infrastructure is stable and top-notch.
There are many hosting providers in the market, so I don’t want to touch on this topic here.
3) Update your Systems
You must have heard this for a long time from quite a big audience because it is vital and necessary.
Updates might contain security improvements or patches for a vulnerability.
Most cyberattacks are automated nowadays. Bots continuously scan your website and are on standby to attack as soon as they find a loophole in your web directory.

Bots attack is one of the main reasons to use website firewall services. These services virtually patch the security loophole as soon as updates are released.
You need to run regular hardware and operating system updates to secure your website from hackers.
4) Use Strong Passwords
There are breached passwords available all over the online platform.
So, there is always a high risk of someone cracking your passwords and compromising your login credentials.

Always be on the alert to secure your website from hackers.
- Do not reuse your password, which has been already used for your other accounts.
- Use a long password with a variety of different characters.
- Try to use random letter combinations for your passwords rather than a dictionary word.
Hackers will use automated bots and software to combine available passwords to generate even more extensive lists of potential passwords.
So, you need to be careful with these types of website security threats.
5) Limit Fewest Privileges Possible
Consider using the minimal set of permissions privileges for your files and folders to perform an action or query. Only grant access to your trusted ones to prevent security risks.
You must carefully define file inclusion rules to limit mistakes. Only highly level authorized people or organizations should be granted access to the system changes.
Try to create single accounts with secure password combinations for everyone on your team with specific access.
So, even accounts get compromised, you can have administrative access to prevent injection attacks.
6) Website Backups
Your website could be hacked, break after an update, or delete critical files by mistake. Disaster can strike anytime. So, you need to protect your website in every step.
So, to avoid these security disasters, the safe options are to run regular backups.
Whether it’s automatic backups or manual, as long as you are doing it right, it doesn’t matter.
Backing up all your websites and databases in one clean stage is crucial irrespective of your hosting provider.
If your website gets hacked or attacked, having a website backup can be useful. These services store your website copy in a secure environment, free of faults or security vulnerabilities.
Implementing an effective website backup process could save your business’s reputation and data from cyberattacks in the long run.
As your business grows or needs upgrades, you need to migrate your content. Website backups can be handy in those situations.
7) Install SSL Certificate
SSL Certificate provides authentication and encryption, reassuring your audiences that their data and transactions are encrypted through a secure socket layer.
SSL Encryption Technology helps to ensure that your information or credentials are sent to the correct server without getting intercepted.
Importance of SSL Certificate;
- Encrypts sensitive information.
- Increases trust with customers.
- Builds brand power.
- Required for PCI compliance for those who accept credit card information on their website.
- Better SEO rankings.
Having an SSL Certificate assures that you care about data security, which provides audiences with extra confidence.
8) Use a Website Security Service
I understand that people sometimes don’t have enough time to take care of every aspect of the website due to their tight schedules.
It’s good to be occupied rather than playing PUBG on your mobile phones. Just saying!
If these situations occur, asking for help from the web security service providers is the right decision.
These companies or organizations are well equipped with website security tools and experts to help you know the security risks.
Before you choose the provider, you might first want to get the answer to this question;
Are the malware cleanups manual or automatic?
Many organizations or companies use automated bots to clean up infections, which are not bad. Still, you need to know that human beings create every technological advancement.
There is a good chance that bots won’t clean every infection. So, you need to pick a provider with professional security analysts working on-site, 24/7.
Additional Questions;
- Is the service charged per site or page?
- What kind of protection can they provide?
- How easy is the setup?
- Is there ongoing protection after the cleanup?
- How do they respond after an incident occurs?
- Do they monitor search engine blacklists?
- Do they stop SEO spam?
- What about virtual patching?
- Is there a limit on cleanup service, or is it unlimited?
- Do they run regular automatic backups?
- Is the website firewall included in the service?
Using a web security service is like paying a premium to your insurance company.
You don’t pay because you expect something wrong to happen, but instead, you pay; if something happens, you have a backup to cover the costs.
Security Practices for Widely Used CMS (WordPress Security)
CMS, usually known as Content Management Systems, is widely used nowadays.
CMS provides a well-structured and functional framework platform for website owners or organizations to create different types of website developments.
Site owners use Content Management Systems for ease of use and low cost compared to custom website development.
Most CMS exploits rely on browsers, so you need to take CMS Security as a serious commitment and perform regular security scans to protect your site.
Top 10 CMS currently in the market;
- WordPress
- Wix
- Squarespace
- Joomla
- Shopify
- Drupal
- Blogger
- Prestashop
- Magneto
- Weebly
Even though there are lots of CMS available in the market, we will discuss the Top Open-Source CMS (WordPress) at the moment.
Don’t worry! The above strategies will help you mitigate risk and protect your website from hackers and security vulnerabilities, whether CMS or custom development.
You should be aware that “Something is always better than Nothing” in the business environment.
WordPress Security
Well! Where to start?
WordPress is an open-source platform that is a big hitter in the website market with the highest CMS share. As of December 2022, WordPress has a 67.15% share in the CMS market.
To clear the confusion, we are talking about wordpress.org, the robust and self-hosted platform.
WordPress isn’t going anywhere, so you can be sure WordPress will be growing over the coming years. With popularity comes the risk of high numbers.
So currently, WordPress websites are among the highly trafficked sites.
I assume you have gone through the above security vulnerabilities and mitigation plan to understand web security. If you haven’t, you can skim through, before, or after this discussion.
Now let’s discuss the security practices you can use to secure your WordPress and stop the attacks.
1) Change the Database Prefix
Before setting up a new WordPress installation, make sure to change the database prefix, which is usually wp_ as a default setting.
You can find these settings in the wp-config.php file. To alter the prefix, change the default setting to your desired name;
$table_prefix = 'wp_';
TO
$table_prefix = 'yourchoice_wp_againyourchoice'
If you already have installed WordPress with the default database prefix, then go through this well-written tutorial on how to change the WordPress database prefix by Zuziko.
Even though you can change the database prefix using Plugins, we don’t recommend it.
2) Rename your Login URL
It’s no surprise that lots of attacks happen on the default login page. Some bots are programmed to recognize and exploit the default WordPress login page.
You can change the Login URL manually, which needs some coding skills. Even though it’s possible to manually change the login page, this is not a good idea for a couple of reasons;
- The login page re-creates a new hash file every time you update WordPress. That means you need to change the URL again.
- Sometimes, it can cause issues with other important site functionality. If it’s a staging site, not a problem, but if it’s a live site, you know the outcome.
Before you test the codes, make sure you have taken a backup because a wrong configuration in wp-login.php can make your website inaccessible.
Manually make changes in the wp-login.php file;
function wp_login_url( $redirect = '', $force_reauth = false ) {
$login_url = site_url( 'wp-login.php', 'login' );
if ( ! empty( $redirect ) ) {
$login_url = add_query_arg( 'redirect_to', urlencode( $redirect ), $login_url );}
if ( $force_reauth ) {
$login_url = add_query_arg( 'reauth', '1', $login_url );}
/**
* Filters the login URL.
* @since 2.8.0
* @since 4.2.0 The `$force_reauth` parameter was added.
* @param string $login_url The login URL. Not HTML-encoded.
* @param string $redirect The path to redirect to on login, if supplied.
* @param bool $force_reauth Whether to force reauthorization, even if a cookie is present.
*/
return apply_filters( 'login_url', $login_url, $redirect, $force_reauth );}
You can use the WPS Hide Login plugin if you don’t want to take the coding hassle, which doesn’t involve manual coding.

This is the plugin we recommend to change the login URL for your website. This plugin is regularly maintained, and the authors quickly address and release the security patches.
3) Remove Default Username Account
Just because there is a default setting doesn’t mean it’s safe to use the default setting for system configurations.
WordPress now usually requires you to select a custom username at the time of setup for a new installation.
However, some organizations offering the famous 1-Click Installation scheme still set the default username to admin, Ufff!
Since you can’t create usernames by default, you can use these steps down below;
- Select Users > Add New from your WordPress Dashboard and then start the process.
- Now, create a new admin username. Don’t forget to delete the old one, and while you delete it, make sure to attribute your content from your old account to the new one if necessary.
- Set the Role to Administrator so that you can delete the old account.
- Use WordPress Plugins (Not Recommended).
- Update username from phpMyAdmin.
Use unique usernames with strong passwords and remove the default admin account in your WordPress installation.
All an attacker needs to do is figure out the password. Then your entire site gets into the evil hands.
4) Use Two-Factor Authentication
You must utilize Two-Factor Authentication for your login credentials to prevent hackers from gaining access to your site.
It acts as an additional security layer. It can be the regular passwords followed by a secret code, secret questions, phone number verifications, or the OTP (One-Time Password) codes.
The popular plugins that do the job well are listed below;
Why does this strategy work? Because it’s almost impossible for attackers to have both your password and your two-factor authentication credentials.
5) Utilize the Security Plugins
Sometimes, it’s better to leave the hard work to the professionals or automated tools so that you can relax your mind and loosen up your schedule.
That’s where WordPress, as CMS, stands out as it has lots of resources to fulfill every demand of the consumers.
There are lots of plugins and vendors working together to create a secure environment for WordPress.
Security plugins can handle a lot of back-end and front-end security protocols for your website.
Some of the features;
- Strict-Transport-Security
- X-Frame-Options
- Active security monitoring
- File scanning
- Malware scanning
- Blacklist monitoring
- Public-Key-Pins
- Content-Security Policy
- X-Content-Type
- WordPress Security hardening
- Post-hack actions
- X-XSS-Protection
- Firewalls
- Compatible settings for Content Delivery Networks (CDNs)
- Brute force attack protection
- Much more…
The popular and rigid WordPress Security Plugins are listed below for your ease;
Ultimately, it’s all about selecting the most reliable way to keep the attackers away from your website.
Some security plugins have price tags. You should consider paying if it's necessary. You should know that there is nothing like a free lunch or a product while doing business.
A security breach on your site can cause some unrecoverable severe damage to your business. So, you need to be one step ahead of the attackers.
6) Choose your Hosting Provider Carefully
As I have already touched on this topic in the above discussion, I want to remind you again that you need to be vigilant while choosing your hosting provider.
As we are talking about WordPress Security, I recommend you choose a hosting provider with separate infrastructures and resources for WordPress websites only.
In general, look for Managed WordPress Hosting providers. These providers custom builts web servers framework with WordPress in mind.
Again, just a few keywords on Google, and you can find lots of providers on the market.
Generally, the company should monitor your sites every minute with tight software-based restrictions in place with 24/7 professional security analysts on-site.
They should protect your site from different malicious attacks and continuously add new security patches every now and then.
7) Regularly Audit WordPress Themes and Plugins
As you know, a coin has two sides. Head and Tail.
Likewise, WordPress has also its Pros and Cons. And those cons usually arise from vulnerable themes and plugins.
You might guess why you should consider auditing themes and plugins.
But believe me, you should never trust anyone 100% in terms of online security.
You should always keep some administrative access only to yourself, which even excludes your team members. Themes and plugins are way out of the league for full trust.
Let me demonstrate this discussion in the example below.
Think WordPress like a White House and Staffs as Themes and Plugins.
You must be aware that the staff has access to the White House with high-grade weapons.
Even though the staff are well trained and paid for their duties, what would happen if the team with full access did something wrong? The outcome would be disastrous.

You can think of the exact scenario with the WordPress environment.
The themes and plugins are working within the WordPress environment, and they have access to the back-end and front-end of your platform.
So, you need to be very careful to grant access. You should always consider using reputable, well-built, durable themes and plugins for your WordPress websites.
The best option would be to do market research and check out the reviews and codes before installing any themes and plugins.
8) Use SSL Technology to Encrypt Data
You need to install SSL technology to encrypt information. From a search engine optimization view, it’s a ranking factor.
You can purchase an SSL Certificate from third parties and install it on your site or purchase it from your hosting provider.
Many web hosting companies provide free or paid SSL Certificates for their clients.

Are there any flaws with free SSLs?
It’s great that organizations are offering free SSL for the good of the Internet. Free encryption technologies are almost the same as paid certificates.
Still, the difference comes down to support, trust, compliance, and many other factors.
You don’t have any warranty or insurance for a free SSL Certificate against fraudulent transactions and other potential issues.
After all, they are providing a free price tag. So, we don’t know when they can exist in the market.
You also need to know that the renewal process is 100% automated, which means your site can be at risk of temporarily being unprotected.
So, if you are ok with all these exceptions, you can go for free certificates. Our only recommended provider would be Let’s Encrypt.

But you should be aware that nothing is free in this world.
In short, you can’t be sure that free SSLs don’t have any flaws.
If you don’t believe us and want proof, you can check the recent blunder of Let’s Encrypt, which affected more than 3 million certificates in an instance.
There are also mentions from big brands why free certificates are a terrible idea.
9) Hardening WordPress Security
Let me inform you that these hardening settings are on an administrative access level, so you need to have full access and must be familiar with some coding.
Don’t worry if you are not familiar with technical terms. I recommend you to use security plugins that don’t need coding skills.
- All In One WP Security and Firewall
- Sucuri Scanner
- Wordfence Security
- Block Bad Queries
- Defender Firewall by WPMU DEV
- Shield Security
- Cerber Security
If you are not comfortable with our suggestions, we recommend using a website firewall service.
As the two leading web server platforms in the current markets are Apache and Nginx servers, we will dive into these two platforms.
Please don't blindly copy and paste these rules, as it may cause you harm if you don't understand how NGINX and APACHE interpret the rules!
You need to backup all your current settings and then implement these rules one by one in your staging site rather than the live site.
There is no certainty that the codes below will work for all the sites. It may work on one website and may not work on other websites.
Let’s dive in with the technical hardening process.
Apache Configurations
1) Hardening .htaccess
Some of the rules and configurations below depend on Apache versions you are running on the web server.
Rewrite Rule – This is to fix issues with permalinks if WordPress has to write access to your server.
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^index\.php$ – [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
Restrict wp-config.php – These rules restrict your wp-config.php from public use.
# Restrict wp-config Apache (Version 2.2)
<files wp-config.php>
order allow,deny
deny from all
</files>
# Restrict wp-config Apache (Version 2.4)
<files wp-config.php>
Require all denied
Require ip Y.Y.Y.Y
</files>
# Disable File Editing
Use the following line of code in the configuration file, wp-config.php, not in .htaccess file.
define('DISALLOW_FILE_EDIT', true);
define('DISALLOW_FILE_MODS', true);
# Force New Sessions Under SSL Protocol
Use the following line of code in the configuration file wp-config.php, not in .htaccess file.
define('FORCE_SSL_LOGIN', true);
define('FORCE_SSL_ADMIN', true);
Block Access to Execution – These rules blocks or restricts access to necessary web directories files.
# Deny Directory Listing
Options - Indexes
# Block Sensitive Files
# protect .htpasswd
<Files ~ "^.*\.([Hh][Tt][Pp])">
Order allow,deny
Deny from all
Satisfy all
</Files>
# Block Installation Files
<files install.php>
Order allow,deny
Deny from all
</files>
<files setup-config.php>
Order allow,deny
Deny from all
</files>
Restrict PHP Execution – These rules restrict attackers from placing backdoors to your important folders in your web directory.
# Backdoor Protection Apache (Version 2.2)
<files *.php>
deny from all
</files>
# Backdoor Protection Apache (Version 2.4)
<filesMatch ".+\.php$">
Require all denied
</filesMatch>
Prevent Image Hotlinking: This rule is essential to save your web server resources. It prevents other websites from using your images hosted on your website.
# Prevent Image Hotlinking
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} \
!^http://(www\.)example.com/.*$ [NC]
RewriteRule \.(svg|gif|jpg|jpeg|bmp|png)$ – [NC,F,L]
Block Include Functions: It restricts malicious or spam files or source codes into folders used for includes.
# Block Includes
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ – [F,L]
RewriteRule !^wp-includes/ – [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ – [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php \– [F,L]
RewriteRule ^wp-includes/theme-compat/ – [F,L]
</IfModule>
Prevent XML-RPC Attacks: If you don’t need any applications or software to connect with WordPress, you can deny access to the xmlrpc.php file.
# Deny Access to xmlrpc.php Completely
<files xmlrpc.php>
Order Deny, Allow
Deny from all
</files>
# Deny Access to xmlrpc.php Partially
<files xmlrpc.php>
order deny, allow
deny from all
allow from X.X.X.X
</files>
Block Information – Although some WordPress guides recommend removing these files altogether, we don’t recommend completely deleting the files.
# Block WordPress Info
<files readme.html>
Order allow,deny
Deny from all
</files>
<files license.txt>
Order allow,deny
Deny from all
</files>
Protect .htaccess – You don’t want attackers to see your hard work in a free environment after doing the hard work.
# Protect .htaccess Apache (Version 2.2)
<files ~ “^.*\.([Hh][Tt][Aa])”>
order allow, deny
deny from all
satisfy all
</files>
# Protect .htaccess Apache (Version 2.4)
<FilesMatch "^.*\.([Hh][Tt][Aa])">
Require all denied
</FilesMatch>
2) Adjust Permissions for Web Directories
As I mentioned above, you need to adjust your configuration correctly to prevent attackers from taking control of your site.
You can adjust these settings directly from an admin panel provided by your hosting provider or through an FTP client.
# Fix Permissions
Permissions for all the directories should be set to 755.
Permissions for all the files should be set to 644.
# Restrict Access to Your Essential Files
wp-config.php file: Set permissions to 600
.htaccess file: Set permissions to 604
As defined in the Unix OS, these permissions or rules are referred to as View, Write, and Execute.
3) Use Security Headers
These lines of codes are inserted in your .htaccess files.
It helps prevent your web pages from being opened in external frames or iframes while preventing clickjacking attacks on your website.
These header settings should be carefully implemented and appropriately checked because it’s easy to block web resources without you noticing.
# X-XSS-Protection
Syntax
X-XSS-Protection: 0
X-XSS-Protection: 1
X-XSS-Protection: 1; mode=block
X-XSS-Protection: 1; report=
Code
header always set x-xss-protection "1; mode=block"
# X-Frame-Options
Syntax
X-Frame-Options: DENY
X-Frame-Options: SAMEORIGIN
X-Frame-Options: ALLOW-FROM hxxps://yourchoice[.]com/
Code
header always set x-frame-options "SAMEORIGIN"
# X-Content-Type-Options
Code
header always set x-content-type-options "nosniff"
# HTTP Strict Transport Security (HSTS)
Strict-Transport-Security: max-age=
Strict-Transport-Security: max-age=; includeSubDomains
Strict-Transport-Security: max-age=; preload
# Content Security Policy (CSP)
Syntax
Content-Security-Policy: ;
Code
Content-Security-Policy: script-src 'self' https://www.google-analytics.com
# Feature-Policy
Syntax
feature-policy: autofocus 'none'; phone 'none'
Code
header always set feature-policy "autoplay 'none'; camera 'none'" always;
When combined, the above codes will look like the settings below:
## CSP
Header set Content-Security-Policy: default-src 'self';
img-src 'self' https://i.imgur.com;
object-src 'none';script-src 'self';
style-src 'self'; frame-ancestors 'self';
base-uri 'self'; form-action 'self';
## General Security Headers
Header set X-XSS-Protection: 1; mode=block
Header set Access-Control-Allow-Origin: https://www.yourchoice.com
Header set X-Frame-Options: deny
Header set X-Content-Type-Options: nosniff
Header set Strict-Transport-Security: max-age=31536000; includeSubDomains
I recommend you perform these tests on different browsers and source frames to check for errors and outcomes before implementing these settings on your live website.
Nginx Configurations
1) Disable Unwanted HTTP Methods
Allowing TRACE or DELETE is risky as it can allow Cross-Site Tracking attack.
if ($request_method !~ ^(GET|HEAD|POST)$)
{
return 405;
}
2) Deny Access to .PHP File Extension and Sub-Directories
You should deny direct access to any PHP files.
location ~* /(?:uploads|files)/.*.php$ {deny all;access_log off;log_not_found off;}
# Works in Sub-Directory Installs and also in Multisite Network
location ~ ^/(?!(blog)/?) {deny all;access_log off;log_not_found off}
3) Block Nginx-Help Log
You don’t want your logs to be open for public viewing.
location ~* /wp-content/uploads/nginx-helper/ {deny all;}
location ~ ^/(wp-includes/js/tinymce/wp-tinymce.php)include /usr/local/nginx/conf/php.conf;
4) Disable Direct Access to Dotfiles
Likewise, a PHP file, a dotfile many contain sensitive information.
location ~ /\.(svn|git)/* {deny all;access_log off;log_not_found off;}
location ~ /\.ht {deny all;access_log off;log_not_found off;}
location ~ /\.user.ini {deny all;access_log off;log_not_found off;}
5) Hide Nginx and PHP versions
This won’t prevent the attack itself. However, don’t let the attacker know your settings.
# Hide the Nginx Version
server_tokens off
# Hide the PHP Version
fastcgi_hide_header X-Powered-By;proxy_hide_header X-Powered-By;
6) Use Security Headers
It provides an extra layer of browser security.
add_header X-Frame-Options "SAMEORIGIN";
add_header Strict-Transport-Security "max-age=31536000";
add_header X-Content-Type-Options nosniff;
add_header X-XSS-Protection "1; mode=block"
7) Disable Directory Listing
You never want anyone to know what’s in the directory for most of the time.
# Disable Directory Listing
autoindex off;
8) Limit Requests to Logins
This rule will limit the number of requests that the page can handle per second.
limit_req_zone $binary_remote_addr zone=WPRATELIMIT:10m rate=5r/s;
location ~ \wp-login.php$ {limit_req zone=WPRATELIMIT;}
9) Deny Access to wp-content Folders
If you think there are some suspicious activities in your database, you can deny access to those files.
location ~* ^/(wp-content)/(.*?)\.(zip|gz|tar|bzip2|7z)\$ {deny all;}
location ~ ^/wp-content/uploads/vigorousitsolution {deny all;}location ~ ^/wp-content/backup {deny all;}
You can utilize the Security Headers website to analyze your HTTP response headers.
Setting headers is relatively quick. You will have a reasonably significant increase in your site security for different attacks on the internet.
## WordPress Security Conclusion ##
As you can see that WordPress Security is a big deal.
So, you can’t ignore the importance of WordPress Security. You need to carefully review the above security checklist and find new ways to improve your website security.
Website Security Mistakes to Avoid
It’s hard to look at every aspect of your website and your business at once.
So, there might be a time that you can make mistakes.
It’s a mistake when you do it unknowingly, but it’s a choice if you repeat the mistakes.
So, try to avoid these mistakes for your website security;
- Do not make the mistake of “I have a small business, or I don’t sell online, so I don’t need to care about my website security” philosophy.
- Do not send the data to an online platform without any encryption technology.
- Do not save your passwords in your browsers. Utilize password management tools instead.
- Do not be too optimistic. Website security is a never-ending process, so you always need to be active and be ready to search and fix the problems.
- Do not install third-party software or tools blindly. You should thoroughly get an overview of the products you want to install beforehand.
- Do not over-rely on website security service providers. It’s not only their responsibility to protect you. You also need to be alert at the same time. They can’t do anything if you do the things they tell you to avoid.
Suppose you have a tight schedule or lack team members to protect your site daily. In that case, it’s a wise decision to get help from experts or web security companies.
On the contrary, you can focus more on your business operations while leaving professionals with hard work.
Website Security FAQs
Why do I need web security? There’s nothing valuable on my site to steal.
Attackers don’t discriminate. It doesn’t only infect popular sites. Most cyberattacks are automated, so you’re as much of a target as anyone.
I don’t need website security now, nothing wrong has happened yet.
Implementing web security is just like locking your home doors. You don’t close the doors because you expect something bad to happen.
You close the doors because the consequences might be devastating if something did happen.
Why should I use the website security service?
Think of this as buying a house. When you buy a home, the house comes with doors and windows with built-in locks.
Still, the house doesn’t have additional security like an alarm system, surveillance camera, and other amenities.
After you move into the house, you’ll likely add different kinds of stuff. You may opt to protect your home by installing additional security protocols, and you’ll pay extra for that added security.
Similarly, as you build your website and add more stuff to it, you’ll want to protect your site by adding another layer of security.
CONCLUSION
As you can see, website security is a big deal. Your site is your source of income or your business for many of you.
So, it’s essential to invest some time and implement some of the security strategies mentioned above.
If you haven’t taken any steps or followed some of the above strategies to secure your website from attacks and vulnerabilities, your site might be at risk.
It doesn’t make sense to cry over spilled milk. So, it’s better to be careful beforehand.
What are your thoughts on website security?
Did I miss some points which you want me to add or update?
Let me know in the comments below.
